Cyber Risk Assessment

Cyber Risk Assessment
Not all companies require a penetration test to successfully evaluate their security posture. Regular vulnerability scans are often an alternative. An engineer performs vulnerability scanning to search systems for known vulnerabilities without exploitation attempts with an end goal of providing a remediation report prioritized on risk.


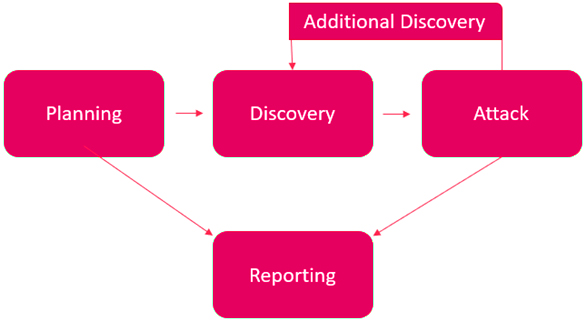
All testing performed is based on the NIST SP 800-115 Technical Guide to Information Security Testing and Assessment, OWASP Testing Guide (v4), and customized testing frameworks. • Planning – Customer goals are gathered and rules of engagement obtained. • Discovery – Perform scanning and enumeration to identify potential vulnerabilities, weak areas, and exploits. • Attack – Confirm potential vulnerabilities through exploitation and perform additional discovery upon new access. • Reporting – Document all found vulnerabilities and exploits, failed attempts, and company strengths and weaknesses.
We help you to increase the security performance of your organization by taking suitable security precautions based on our IT risk assessment. With the implementation of measures (e.g. encryption) you make your IT processes and systems more secure.